© Edm
Last month, a joint international operation, known as Eastwood and coordinated by Europol and Eurojust, targeted the cybercrime network NoName057(16). Law enforcement and judicial authorities from Czechia, France, Finland, Germany, Italy, Lithuania, Poland, Spain, Sweden, Switzerland, the Netherlands and the United States took simultaneous actions against offenders and infrastructure belonging to the pro-Russian cybercrime network. The investigation was also supported by ENISA, as well as Belgium, Canada, Estonia, Denmark, Latvia, Romania and Ukraine. The private parties ShadowServer and abuse.ch also assisted in the technical part of the operation.
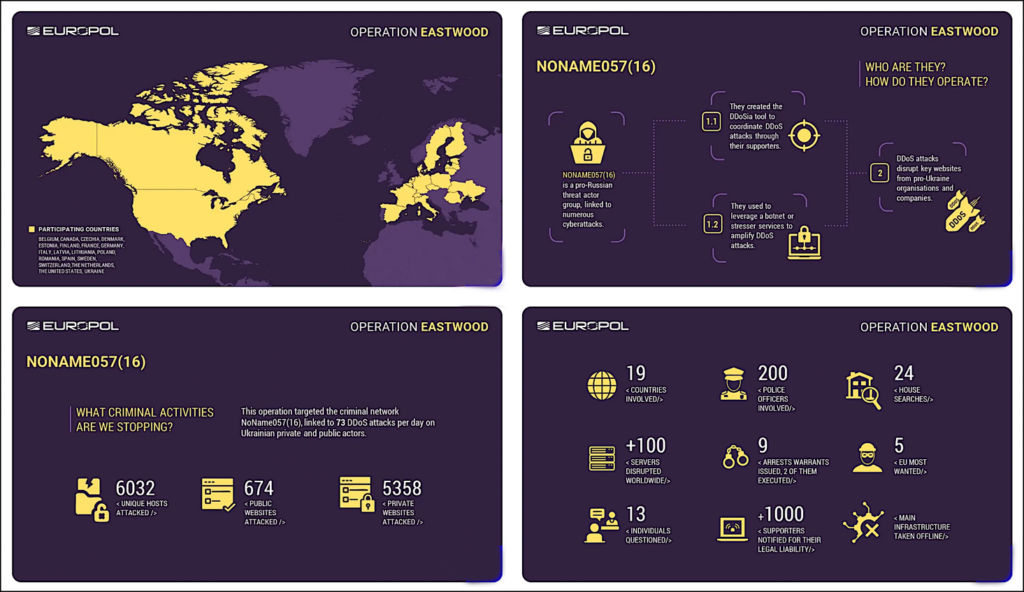
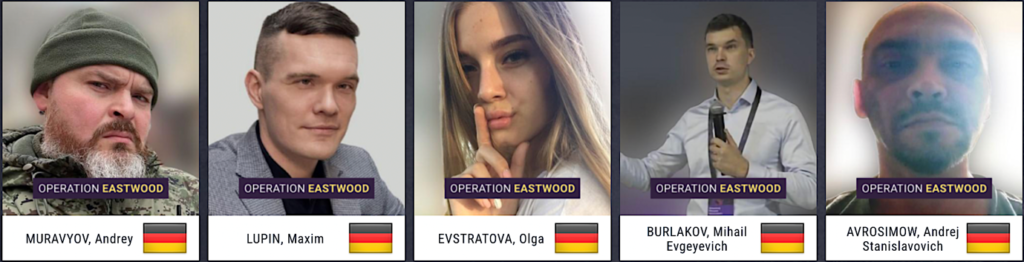
The actions led to the disruption of an attack-infrastructure consisting of over one hundred computer systems worldwide, while a major part of the group’s central server infrastructure was taken offline. Germany issued six warrants for the arrest of offenders living in the Russian Federation. Two of these persons are accused of being the main instigators responsible for the activities of “NoName057(16)”. In total, national authorities have issued seven arrest warrants, which are directed, inter alia, against six Russian nationals for their involvement in the NoName057(16) criminal activities. All of the suspects are listed as internationally wanted, and in some cases, their identities are published in media. Five profiles were also published on the EU Most Wanted website.
National authorities have reached out to several hundred of individuals believed to be supporters of the cybercrime network. The messages, shared via a popular messaging application, inform the recipient of the official measures highlighting the criminal liability they bear for their actions pursuant to national legislations. Individuals acting for NoName057(16) are mainly Russian-speaking sympathisers who use automated tools to carry out distributed denial-of-service (DDoS) attacks. Operating without formal leadership or sophisticated technical skills, they are motivated by ideology and rewards.
NoName057(16) has professed support for the Russian Federation since the start of the war of aggression against Ukraine. Since the start of the war, it has executed multiple DDoS attacks against critical infrastructure during high-level (political) events. The group has also exhibited anti-NATO and anti-U.S. sentiment. During a DDoS attack, a website or online service is flooded with traffic, overloading its capacity and thus making it unavailable. The hacktivist group has executed 14 attacks in Germany, some of them lasting multiple days and affecting around 230 organisations including arms factories, power suppliers and government organisations. Attacks were also executed across Europe during the European elections. In Sweden, authorities and bank websites were targeted, while in Switzerland multiple attacks were carried out during a video message given by the Ukrainian President to the Joint Parliament in June 2023, and during the Peace Summit for Ukraine in June 2024. Most recently, the Netherlands was targeted during the NATO Summit at the end of June.
To execute their attacks, the group recruited supporters through a messaging service. It is estimated that the hackers were able to mobilise around 4000 users who supported their operations by downloading malware that made it possible for them to participate in the DDoS attacks. The group also built its own botnet using hundreds of servers around the world that increased the attack load, causing more damage.
Coordination of the many international partners was crucial for the success of the operation. Through Eurojust, authorities were able to coordinate their findings and plan an action day to target the hacktivist group. The Agency ensured that multiple European Investigation Orders and Mutual Legal Assistance processes were executed. During the action day Eurojust coordinated any last-minute judicial requests that were needed during the operation.
Europol facilitated the information exchange, supported the coordination of the operational activities and provided extended operational analytical support, as well as crypto tracing and forensic support during the lent of the investigation, and coordinated the prevention and awareness raising campaign, released to unidentified yet offenders via messaging apps and social media channels. During the action day, Europol set-up a Command Post at Europol’s headquarters and made available a Virtual Command post for online connection with the in-person Command.
The investigation culminated in an action day where actions targeting the group took place in eight countries. Authorities were able to disrupt of over 100 servers worldwide. Searches took place in Germany, Latvia, Spain, Italy, Czechia, Poland and France to gather evidence for the investigation. Additionally, authorities informed the group and 1100 supporters and 17 administrators about the measures taken and the criminal liability they bear for their actions. Seven international arrest warrants have been issued. Germany issued six warrants which are directed inter alia against suspects living in the Russian Federation. Two suspects are accused of being the main instigators responsible for the activities of NoName057(16).

